Evaluation of portable near-infrared spectroscopy for authentication of mRNA based COVID-19 vaccines
City Research Online - Continuous face authentication scheme for mobile devices with tracking and liveness detection
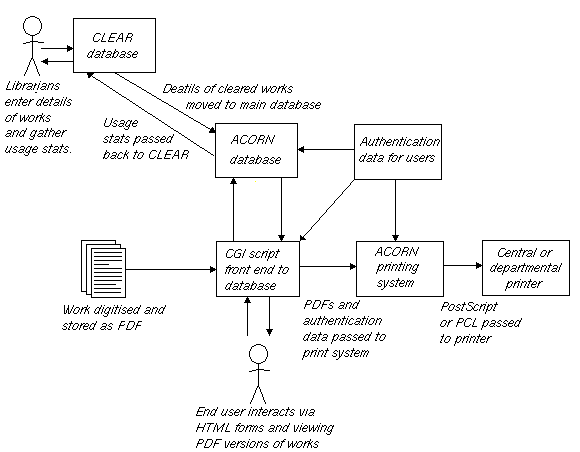
Multidimensional: User with File Content and Server's status based Authentication for Secure File Operations in Cloud - Sheffield Hallam University Research Archive

A Second Mona Lisa?: Challenges of Attribution and Authentication and Various Possibilities for Evaluating a Work of Art: 27 (L'Ermarte): Amazon. co.uk: Lorusso, Salvatore, Natali, Andrea, Isbouts, Jean-Pierre, Asmus, John, Parfenov, Vadim, Lorusso,
Multi-Factor Authentication for Shibboleth Identity Providers - Sheffield Hallam University Research Archive

British Art Authentication Investigation Experts || UK Artist Attribution Services || Specialist Provenance Verification ~ Fraud & Forgery Identification ~ Due Diligrnce